Deploying a vIDM clustered environment using NSX-T Loadbalancer
- Arun Nukula
- Jun 27, 2022
- 4 min read
Updated: Jun 30, 2023
Documenting steps taken to install a vIDM ( Workspace One ) in my lab so that it would benefit others too
Step-1 : Certificate Creation in Locker
Create a certificate inside vRSLCM Locker. This would be your vIDM certificate
Enter all information which is needed to create a certificate in the locker
You must enter the load balancer name of in the CN field
Under IP and Hostname section , enter all hostnames which belongs to vIDM cluster including Load Balancer


Once certificate is created , click on the three dots next to the certificate and then download it

A .pem file will be downloaded
Edit the .pem file with the notepad
The first section would be server certificate followed by root certificate. In my case root certificate is from vRSLCM's locker.
The last section would be the private key.
Copy the root certificate and create a separate cert called root.cer and then create a seperate file with server certificate and the key and call itas server certificate with key.
Step:2 Importing certificates into NSX-T
Login into NSX-T and then click on system to import the certificate files saved before
root certificate
server certificate with key

root certificate should be imported as CA cert and then server certificate as certificate

Step:3 Create Service Monitors
You set up health check monitoring.Servers that fail to respond to the health checks within a specified time period are excluded from future connection handling.
In a Web browser, log in to NSX-T Manager for the Management domain by using the user interface.
On the main navigation bar, click Networking.
In the navigation pane, click Load balancing and click the Monitors tab.
From the Select monitor type drop-down menu, select Active.
From the Add active monitor drop-down menu, select HTTPS and configure the settings.
Setting | Value |
Name | didmmonitor |
Protocol | HTTPS |
Monitoring Port | 443 |
Monitoring Interval | 3 |
Timeout Period | 10 |
Description | Monitor for Distributed vIDM or WS1 |
Falls Count | 3 |
Rise Count | 3 |
In the HTTP request section, click Configure
The HTTP request and response configuration dialog box opens.
On the HTTP request configuration tab, configure the settings
Setting | Value |
HTTP Method | Get |
HTTP request URL | /SAAS/API/1.0/REST/system/health/heartbeat |
HTTP request version | 1.1 |
On the HTTP response configuration tab, configure the settings, and click Apply
Setting | Value |
HTTP response code | 200 |
HTTP response body | ok |
In the SSL configuration section, click Configure.
Setting | Value |
Server SSL | Enabled |
Client certificate | Select the server certificate with key |
Server SSL Profile | default-balanced-server-ssl-profile |
On the Monitors page, click Save




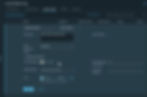
Step:4 Creating Server Pool
The server pool determines the load balancing algorithm and combines resources from the pool members.
You add the three Workspace ONE Access cluster nodes as members of the server pool.
Name | IP Address |
didmone.example.com | 10.xx.xx.1 |
didmtwo.example.com | 10.xx.xx.2 |
didmthree.example.com | 10.xx.xx.3 |
In a Web browser, log in to NSX-T Manager for the Management domain by using the user interface
On the main navigation bar, click Networking.
In the navigation pane, click Load balancing, click the Server pools tab, and click Add server pool.The Add new server pool wizard opens.
On the General properties page, configure the settings
Setting | Value |
Name | didmserverpool |
Description | Server Pool for vIDM or WS1 |
Algorithm | Least Connection |
Translation Mode | Automap |
Click Select Members
On the Configure server pool members page, click Add member, configure the settings, click Save, and click Apply
Setting | Value for didmone | Value for didmtwo | Value for didmthree |
Name | didmone | didmtwo | didmthree |
IP | 192.xx.xx.1 | 192.xx.xx.2 | 192.xx.xx.3 |
Port | 443 | 443 | 443 |
Weight | 1 | 1 | 1 |
State | Enabled | Enabled | Enabled |
Backup Member | Disabled | Disabled | Disabled |
Maximum concurrent connections | - | - | - |
Click Set Monitors, on the Select health monitors page, select didmmonitor, and click Apply..
On Server Pool page, click Apply


Step:5 Create Application Profiles
You create an application profile and associate it with a virtual server to define the behavior of a particular type of network traffic. The virtual server then processes traffic according to the values specified in the profile.
In a Web browser, log in to NSX-T Manager for the Management domain by using the user interface.
Create the application profiles for Workspace ONE Access or vIDM cluster
On the main navigation bar, click Networking.
In the navigation pane, click Load balancing and click the Profiles tab.
From the Select profile type drop-down menu, select Application.
From the Add application profile drop-down menu, select HTTP Profile, configure the settings, and click Save.
Setting | Value for Application Profile | Value for Application Profile Redirect |
Name | didmhttpappprofile | didmhttpappprofileredirect |
Type | HTTP | HTTP |
Idle Timeout | 3600 | 3600 |
Descriotion | vIDM & WS1 App Profile | vIDM & WS1 App Profile Redirect |
X-Forwarded-For | Insert | none |
Request Header Size | 1024 | 1024 |
Response Header Size | 4096 | 4096 |
Redirection | None | HTTP to HTTPS Redirect |
Response Timeout | 60 | 60 |
NTLM Authentication | Disabled | Disabled |

Create a persistence profile for the cross-region Workspace ONE Access cluster.
On the Load balancing page, click the Profiles tab.
From the Select profile type drop-down menu, select Persistence.
From the Add persistence profile drop-down menu, select Cookie, configure the settings,
and click Save.
Setting | Value |
Name | didmcookiepersistenceprofile |
Description | Cookie Persistence Profile |
Share Persistence | Disabled |
Cookie Mode | Rewrite |
Cookie Name | JSESSIONID |
Cookie Garbling | Enabled |
Cookie Fallback | Enabled |

Step:6 Creating Virtual Servers
You create two L7 HTTP virtual servers for the cross-region Workspace ONE Access cluster. These virtual servers are associated with the configured application profile and server pool and distribute client connections among the server pool members.
In a Web browser, log in to NSX-T Manager for the Management domain by using the user interface.
On the main navigation bar, click Networking.
In the navigation pane, click Load balancing and click the Virtual servers tab.
From the Add virtual server drop-down menu, select L7 HTTP and configure the settings
Setting | Value |
Name | didmvirtualserver |
IP Address | IP of the VIP |
Ports | 443 |
Load Balancer | select appropriate lb in your environment |
Server Pool | select the server pool created in previous step |
Description | Virtual Server Pool for vIDM or WS1 |
Application Profile | Select Application Profile created previously |
Persistence | Cookie |
Cookie | Select the persistence profile created previously |
In the SSL Configuration section, click Configure
The Edit SSL configuration dialog box opens.
Click the Client SSL tab and configure the settings
Setting | Value |
Client SSL | Enabled |
Default Certificate | select the server certificate for vIDM |
Client SSL Profile | default-balanced-client-ssl-profile |
Click the Server SSL tab, configure the settings, and click Save
Setting | Value |
Server SSL | Enabled |
Client Certificate | select the server certificate for vIDM |
Server SSL Profile | default-balanced-server-ssl-profile |
Remember to select root certificate for LCM or any custom CA if your using your own certificate under Advanced Properties on both Client and Server SSL


Expand the Load balancer rules section.
Next to the Request rewrite phrase section click Set.The Set load balancer rules wizard opens.
Click the Request rewrite tab, click Add rule, configure the settings, and click Save
Setting | Value |
Match Conditions | Delete Any Match Conditions |
Match Strategy | All |
Action | HTTP Request Header Rewrite |
Header Name | Remote Port |
Header Value | $_remote_port |

On Set load balancer rules page, click Apply.
On the Virtual servers page, click Save.
From the Add virtual server drop-down menu, select L7 HTTP, configure the settings, and click Save.
Settings | Value |
Name | didmvirtualserverredirect |
IP Address | IP of the VIP |
Ports | 80 |
Load Balancer | Select Load Balancer based on your environment |
Sevrer Pool | - |
Description | Virtual Server for HTTP to HTTPS Redirect |
Application Profile | Select the redirect application profile created before |
Persistence | Disabled |

This concludes NSX-T Load Balancer configuration for vIDM or Workspace One
Step:7 Installing vIDM through vRSLCM
Click on "Create Environment"
Enable the trigger which says "Enable to Install/Import Identity Manager"
Select the password , this is the default password
Datacenter where it's to be provisioned
Click on next to select "New Install" for vIDM. Choose Version and then the deployment type to be a cluster
Accept EULA
Select the certificate we created from Locker
Select the vCenter Server , Cluster , Network , Datastore and Disk Mode as per your requirements
Enter Default Gateway , Netmask , DNS and Search Path information along with DNS Server selection
In the next pane you have map / enter all product properties like
Selection of Certificate , select the certificate created before in locker
Node Size , would be selecting Medium
FIPS Compliance Mode , I'd leave it OFF
Admin Password , I'd leave it to the default installer password
Default Configuration Admin email would be configadmin@vsphere.local
Default Configuration Admin username would be configadmin
Default COnfiguration Admin password would be same as before , installer password
I'd leave Sync Group Members ticked / selected
In the Cluster Virtual IP Section , enter the FQDN and Delete IP for Database
Under Components Section , enter VM Name , FQDN and IP Address of all the three nodes
Perform Manual Validations

Go ahead and check the box when manual validations are complete and ensure precheck is all good and green to move forward

Submit the Request for deployment
Step:8 vIDM Distributed Installation Completion


